Access Control
Access Control settings section enables you to configure security related aspects of Identity and Access Management module.
In this article, you can find instructions on:
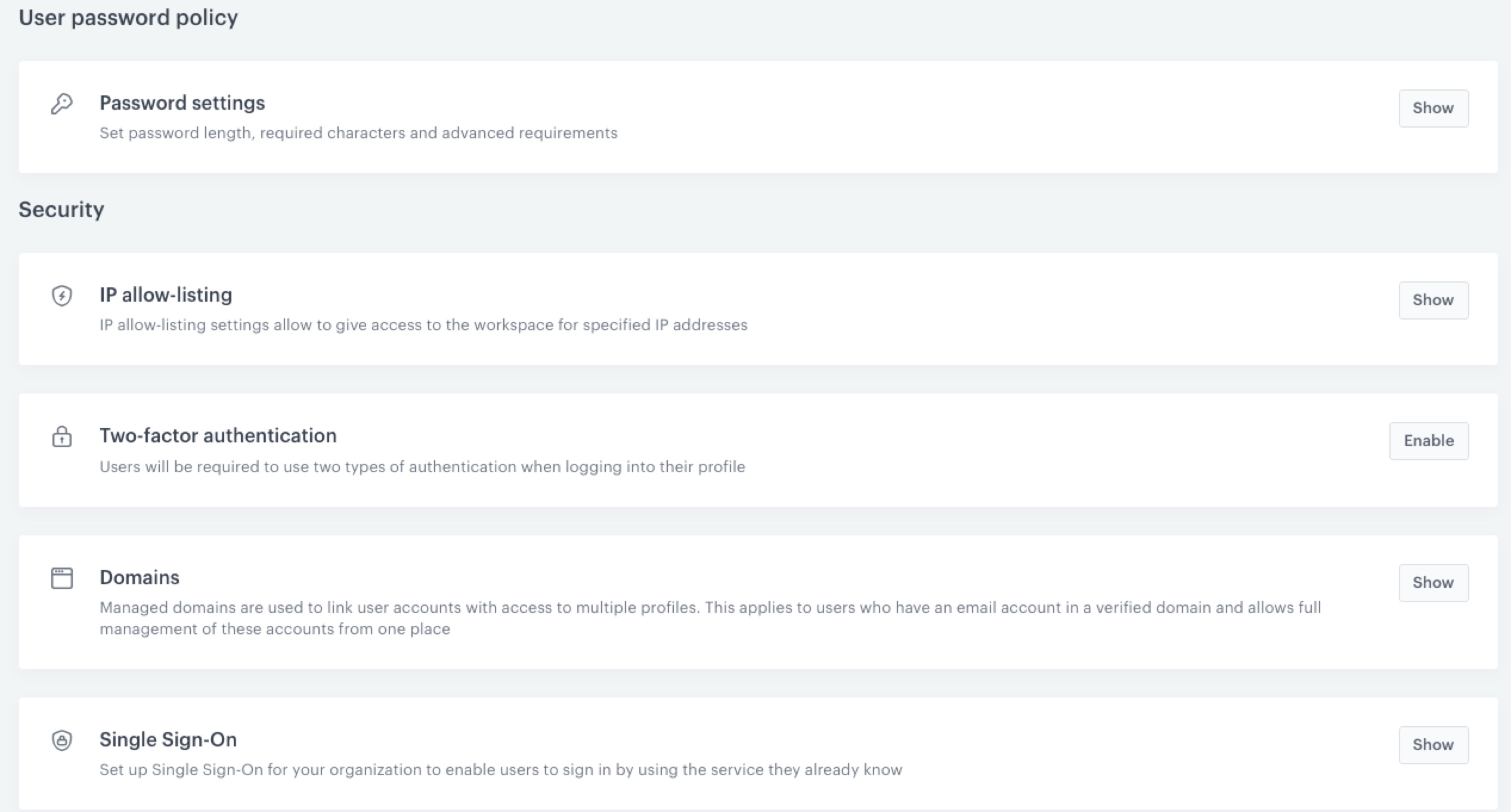
- Password settings - To define the strength of user’s passwords
- IP allow-listing - To define the list of IP addresses from which users can log in to your workspace
- Two-factor authentication - To force users added to your workspace to confirm their credentials through a mobile authentication app
- Domain management - It is required if you want to have greater capabilities to manage users (registerd within the verified domain) in your workspace
- Single sign-on - To allow users to authenticate once with your IdP and then access Synerise or other enabled Service Providers, without the necessity to authenticate with each of those applications separately.
Prerequisites
- You must be granted a set of permissions that allow access to Settings and editing within this module.
- For Two factor authentication: Download any Time-Based One Time Password (TOTP) authentication mobile app (applies to all users of a workspace in which this type of authentication is enforced).
- For Managed domains: You must have access to domain management or to the root folder in the hosting behind the domain.
- For Single Sign-on:
- You must verify the ownership of at least one domain (could be more if needed).
- Create a backup user that won’t be using the same email address in the Identity Provider account. This is not required if you start with the Allow signing in with both methods authentication mode (explained here.
- You must be granted user permissions to access Settings and configure Identity provider.
- You must have access to Identity Provider’s admin panel to configure SAML application.
Note:
You will need the data from the Identity Provider. For details on using the IdP’s application, refer to the IdP’s documentation
You will need the data from the Identity Provider. For details on using the IdP’s application, refer to the IdP’s documentation